Saturday, August 11, 2007
Simple Tweaks For Peak Pc Graphics Performance
New PCs often support 32-bit color, which offers the same 16 million-plus colors as True Color. The extra 8 bits control image opacity. This is useful in fast-moving 3D games but of little help in most business apps.
Refresh rate: Expressed in hertz, or cycles per second, this tells how often the phosphors that glow to create an image on a CRT screen are reenergized--that is, the times per second that the screen's image is redrawn. A refresh rate that's too low can cause annoying screen flicker. Even if you don't see the flicker, slow refreshes can cause eyestrain and headaches.
Conventional wisdom says your refresh rate should be no less than 72 Hz. Some experts say the minimum rate is 80 Hz. Try different refresh rates until you find the one that works for you. Note that if your refresh rate is too high, you could lose image opacity. Still, few of us can discern rates higher than 85 Hz.
To adjust your screen's refresh rate in Windows XP, open Display Properties and click Settings, Advanced, Adapter, List All Modes. Pick a combination of refresh rate, screen resolution, and color depth from the list of supported values.
To change your refresh rate in other versions of Windows, open Display Properties and then click Settings, Advanced, Adapter. Select an option from the 'Refresh rate' drop-down menu. If you see no options there, however, your graphics board and monitor don't support multiple refresh rates.
Even in that case, you might be able to increase your display's refresh rate by decreasing your screen resolution or your color depth. All three specs compete for graphics-processing capacity, so if your graphics system is running at its maximum, try increasing one setting and lowering another. For example, reducing color depth from 32-bit to 16-bit--no big deal if you never look at photos--may free up enough processing power to let you bump your refresh rate from an annoying 60 Hz to an eye-pleasing 72 Hz. Or you may be able to increase resolution from 800 by 600 to 1024 by 768. There's no guarantee, but these tricks might work.
Windows automatically sets your screen refresh rate to a safe but slow 60 Hz when it can't detect your monitor. To confirm that Windows XP correctly recognizes your monitor, open Display Properties and click Settings, Advanced, Monitor. If your monitor isn't listed under 'Monitor type', download and install the device's driver from the manufacturer's Web site.
In other versions of Windows, verify that Plug and Play is enabled. Make sure your monitor is listed under 'Display' on the Settings tab in Display Properties, and then click Advanced, Monitor. Verify that Automatically detect Plug & Play monitors is checked. If it isn't, select it and then reset your refresh rate to a level that is higher than Windows' default 60 Hz.
DirectX: This Windows component controls multimedia functions. To check your current DirectX version, click Start, Run, type dxdiag, and click OK. Choose the System tab and look under System Information on the lower part of the screen. DirectX 9 is the latest version; if you don't have it, download it from Microsoft.
Touch Those Dials!
You can improve the image quality of your monitor via its built-in controls. The options vary by display manufacturer and model, but you should find brightness and other controls on most monitors.
Adjust brightness and contrast: Use this gray-scale image on your screen. Be sure you can see as many of the image's 17 shades as possible; the two or three darkest may be tough to view in a bright room.
Center and align: Few monitors come straight from the factory with optimal screen geometry. Use your monitor's screen-placement controls to center your displayed image, keep its edges straight, and minimize unfilled screen space.
To avoid eyestrain and other physical problems, put the top of the screen at eye level and at arm's length from your head (your best position may vary). Orient your screen to avoid glare from lights and windows. If that's not possible, get a glare filter such as Kensington's $34 GlareMaster.
Clean it: Gently wipe your screen with a soft, lightly moistened cloth. Unless the monitor is really filthy, avoid cleaning solutions, which can damage delicate screen coatings. Clean the dust from the cooling vents in the monitor's case; overheating is your display's lethal enemy.
Graphics Triage
If your screen goes blank, the problem is likely due to a disconnected monitor cable, an unplugged power cord, or a too-low brightness setting. Monitors do die, however. If you smell something burning or hear popping sounds, your monitor could be failing--turn it off immediately. Monitors have been known to spontaneously combust.
Corrupted graphics drivers cause all kinds of PC problems. To check for a damaged graphics driver, install the plain-vanilla VGA driver that comes with Windows. If your troubles disappear, reinstall a clean copy of the monitor's original driver, or an updated version.
Some graphics boards don't work or play well with other hardware devices. Windows allows you to disable graphics-acceleration functions for the sake of compatibility. Open Display Properties and click Settings, Advanced, Troubleshooting in Windows XP and 2000, or Settings, Advanced, Performance in Windows 98 and Me. Move the slider under 'Hardware acceleration' to the left to disable your graphics acceleration.
A shaking or shimmering image on your screen may be due to nearby magnetic fields. Keep clocks and other appliances that use electric motors, and those that use a lot of electricity (such as microwave ovens), far from your monitor. Power lines behind walls can cause interference, so try moving the display away from nearby walls.
If your screen image is washed in blue, red, or green, check for a loose cable connecting your graphics board to your monitor. Look for bent pins inside the cable connector; you can often straighten them with needle-nose pliers. If on-screen objects have a rainbow cast, some monitors have convergence controls that you can use to tune the image.
Living in a Flat World
Notebook displays are fine-tuned in the factory to work with the system's other hardware; your desktop's flat panel likely isn't. And tuning an LCD isn't the same as tuning a CRT monitor. If both your LCD and graphics board support Digital Visual Interface connections, make sure they're using them. Vendors don't always ship a DVI cable with cards that produce both analog and digital signals, so you'll have to replace the analog cable. If your display supports DVI but your graphics card doesn't, upgrade your card.
Make sure your LCD is set to its native resolution. Many flat-panel displays don't look good at other resolutions. Unfortunately, some 15-inch LCDs have a native resolution of 1024 by 768 dpi, which makes text minuscule. The solution is to open Display Properties, click Appearance, and change the setting on the 'Font size' drop-down menu to increase the size of your text. (Most browsers include their own font-size settings.)
In Windows XP, open Display Properties, click Appearance, Effects, and check Use the following method to smooth screen fonts. Select ClearType to see a big improvement in the appearance of many of your fonts.
Cracking Zip Password Files
FZC uses multiple methods of cracking - bruteforce (guessing passwords systematically until the program gets it) or wordlist attacks (otherwise known as dictionary attacks. Instead of just guessing passwords systematically, the program takes passwords out of a "wordlist", which is a text file that contains possible passwords. You can get lots of wordlists at _www.theargon.com.).
FZC can be used in order to achieve two different goals: you can either use it to recover a lost zip password which you used to remember but somehow forgot, or to crack zip passwords which you're not supposed to have. So like every tool, this one can be used for good and for evil.
The first thing I want to say is that reading this tutorial... is the easy way to learn how to use this program, but after reading this part of how to use the FZC you should go and check the texts that come with that program and read them all. You are also going to see the phrase "check name.txt" often in this text. These files should be in FZC's directory. They contain more information about FZC.
FZC is a good password recovery tool, because it's very fast and also support resuming so you don't have to keep the computer turned on until you get the password, like it used to be some years ago with older cracking programs. You would probably always get the password unless the password is longer than 32 chars (a char is a character, which can be anything - a number, a lowercase or undercase letter or a symbol such as ! or &) because 32 chars is the maximum value that FZC will accept, but it doesn't really matter, because in order to bruteforce a password with 32 chars you'll need to be at least immortal..heehhe.. to see the time that FZC takes with bruteforce just open the Bforce.txt file, which contains such information.
FZC supports brute-force attacks, as well as wordlist attacks. While brute-force attacks don't require you to have anything, wordlist attacks require you to have wordlists, which you can get from _www.theargon.com. There are wordlists in various languages, various topics or just miscellaneous wordlists. The bigger the wordlist is, the more chances you have to crack the password.
Now that you have a good wordlist, just get FZC working on the locked zip file, lie down and wait... and wait... and wait...and have good thoughts like "In wordlist mode I'm gonna get the password in minutes" or something like this... you start doing all this and remember "Hey this guy started with all this crap and didn't say how I can start a wordlist attack!..." So please wait just a little more, read this tutorial 'till the end and you can do all this "crap".
We need to keep in mind that are some people might choose some really weird passwords (for example: 'e8t7@$^%*gfh), which are harder to crack and are certainly impossible to crack (unless you have some weird wordlist). If you have a bad luck and you got such a file, having a 200MB list won't help you anymore. Instead, you'll have to use a different type of attack. If you are a person that gives up at the first sign of failure, stop being like that or you won't get anywhere. What you need to do in such a situation is to put aside your sweet xxx MB's list and start using the Brute Force attack.
If you have some sort of a really fast and new computer and you're afraid that you won't be able to use your computer's power to the fullest because the zip cracker doesn't support this kind of technology, it's your lucky day! FZC has multiple settings for all sorts of hardware, and will automatically select the best method.
Now that we've gone through all the theoretical stuff, let's get to the actual commands.
--------------------------------------------------------------------------------
Bruteforce
--------------------------------------------------------------------------------
The command line you'll need to use for using brute force is:
fzc -mb -nzFile.zip -lChr Lenght -cType of chars
Now if you read the bforce.txt that comes with fzc you'll find the description of how works Chr Lenght and the Type of chars, but hey, I'm gonna explain this too. Why not, right?... (but remember look at the bforce.txt too)
For Chr Lenght you can use 4 kind of switches...
-> You can use range -> 4-6 :it would brute force from 4 Chr passwors to 6 chr passwords
-> You can use just one lenght -> 5 :it would just brute force using passwords with 5 chars
-> You can use also the all number -> 0 :it would start brute forcing from passwords with lenght 0 to lenght 32, even if you are crazy i don't think that you would do this.... if you are thinking in doing this get a live...
-> You can use the + sign with a number -> 3+ :in this case it would brute force from passwords with lenght 3 to passwords with 32 chars of lenght, almost like the last option...
For the Type of chars we have 5 switches they are:
-> a for using lowercase letters
-> A for using uppercase letters
-> ! for using simbols (check the Bforce.txt if you want to see what simbols)
-> s for using space
-> 1 for using numbers
Example:
If you want to find a password with lowercase and numbers by brute force you would just do something like:
fzc -mb -nzTest.zip -l4-7 -ca1
This would try all combinations from passwords with 4 chars of lenght till 7 chars, but just using numbers and lowercase.
*****
hint
*****
You should never start the first brute force attack to a file using all the chars switches, first just try lowercase, then uppercase, then uppercase with number then lowercase with numbers, just do like this because you can get lucky and find the password much faster, if this doesn't work just prepare your brain and start with a brute force that would take a lot of time. With a combination like lowercase, uppercase, special chars and numbers.
--------------------------------------------------------------------------------
Wordlis
--------------------------------------------------------------------------------
Like I said in the bottom and like you should be thinking now, the wordlist is the most powerfull mode in this program. Using this mode, you can choose between 3 modes, where each one do some changes to the text that is in the wordlist, I'm not going to say what each mode does to the words, for knowing that just check the file wlist.txt, the only thing I'm going to tell you is that the best mode to get passwords is mode 3, but it takes longer time too.
To start a wordlist attak you'll do something like.
fzc -mwMode number -nzFile.zip -nwWordlist
Where:
Mode number is 1, 2 or 3 just check wlist.txt to see the changes in each mode.
File.zip is the filename and Wordlist is the name of the wordlist that you want to use. Remember that if the file or the wordlist isn't in the same directory of FZC you'll need to give the all path.
You can add other switches to that line like -fLine where you define in which line will FZC start reading, and the -lChar Length where it will just be read the words in that char length, the switche works like in bruteforce mode.
So if you something like
fzc -mw1 -nztest.zip -nwMywordlist.txt -f50 -l9+
FZC would just start reading at line 50 and would just read with length >= to 9.
Example:
If you want to crack a file called myfile.zip using the "theargonlistserver1.txt" wordlist, selecting mode 3, and you wanted FZC to start reading at line 50 you would do:
fzc -mw3 -nzmyfile.zip -nwtheargonlistserver1.txt -f50
--------------------------------------------------------------------------------
Resuming
--------------------------------------------------------------------------------
Other good feature in FZC is that FZC supports resuming. If you need to shutdown your computer and FZC is running you just need to press the ESC key, and fzc will stop. Now if you are using a brute force attack the current status will be saved in a file called resume.fzc but if you are using a wordlist it will say to you in what line it ended (you can find the line in the file fzc.log too).
To resume the bruteforce attack you just need to do:
fzc -mr
And the bruteforce attack will start from the place where it stopped when you pressed the ESC key.
But if you want to resume a wordlist attack you'll need to start a new wordlist attack, saying where it's gonna start. So if you ended the attack to the file.zip in line 100 using wordlist.txt in mode 3 to resume you'll type
fzc -mw3 -nzfile.zip -nwwordlist.txt -f100
Doing this FZC would start in line 100, since the others 99 lines where already checked in an earlier FZC session.
Well, it looks like I covered most of what you need to know. I certainly hope it helped you... don't forget to read the files that come with the program
Converting to NTFS
The recommended option:
There are a number of features in Windows XP that will only work if the NTFS file system is present, which is why it’s suggested you make use of it. File and folder permissions, encryption and privacy options are just some of those you’ll be able to access. In particular, those of you who have set up user accounts will find NTFS invaluable. For instance, if you continue to use FAT or FAT32 anyone with physical access to the drive will be able to access the files and folders that are stored there. However, with NTFS you’ll be able to use a level of encryption (Professional Edition only) that will enable you to protect your data.
You’ll also find NTFS more reliable in that it’s more able to recover from disk errors than its FAT or FAT32 counterparts. A log of all disk activity is kept so should a crash occur, Windows XP can use this information to repair the file system when your PC boots up again. To find out what file system you’re using, open My Computer, right-click your main hard drive and choose Properties. Take a look at the General tab to see confirmation of the file system that’s in use.
Convert now:
You can use the convert tool in Windows XP to change the file system on your hard disk from FAT or FAT32 to NTFS. The whole process is safe and your existing data won’t be destroyed. To begin, click Start -> Run, type cmd and press [Return]. At the command prompt type convert c: /fs:ntfs and press [Return] (where ‘c’ is the letter of the drive you’re converting). When you try and run the convert utility, it’s likely that Windows XP will be using your paging file so the process won’t be completed immediately. Therefore, you’ll see a brief message on screen informing you that the conversion will take place instead the next time Windows starts up. Having restarted, the Check Disk utility will run, the conversion will be performed automatically and you may find that your PC will reboot twice more.
The benefits:
With your drive now running NTFS, it’s time to take advantage of the new options that are available. Having created a number of different user accounts you can now control the level of access that’s granted to individual users. For example, there are going to be certain files and folders that you’ll want some users to be able to access but not others. If you have Windows XP Professional Edition you can do this immediately.
Right-click any file or folder, choose Properties and select the Security tab. A dialog will be displayed showing the names of all your users. Alongside will be two columns which enable you to select levels of access for each of them, the permissions include Full Control, Modify, Read and Write. You can then check the appropriate box to determine whether or not to Allow or Deny a particular permission. For Windows XP Home Edition users, the Security tab won’t be immediately available. To access this option you’ll need to restart your PC, pressing [F8] until a menu appears. Next select Safe Mode and wait for Windows XP to start up. You can then set your options in the same way.
Another feature is NTFS compression. It’s quick and seamless as your file or folder is decompressed automatically when you access it. (Don’t confuse this with a Zip compression utility where the files need to be extracted before they can be accessed.) Although you may have used NTFS compression on a file or folder, there’s no way of telling just by looking at it. To remedy this, open My Computer, click Tools -> Folder Options and select the View tab. Under Advanced settings, scroll down and check the option ‘Show encrypted or compressed NTFS files in color’, then click Apply and OK. Take a look at your compressed items in My Computer and you’ll see the text label has changed from black to blue. Something else that’s exclusive to Professional Edition users is the Encrypting File System (EFS). You can use this to protect your important data so that no one else can read it. Your encrypted files and folders will only be accessible when you have logged into your user account successfully.
Best Keyboard Shortcuts
Type the following commands in your Run Box (Windows Key + R) or Start Run
This is usually followed by:
devmgmt.msc = Device Manager
msinfo32 = System Information
cleanmgr = Disk Cleanup
ntbackup = Backup or Restore Wizard (Windows Backup Utility)
mmc = Microsoft Management Console
excel = Microsoft Excel (If Installed)
msaccess = Microsoft Access (If Installed)
powerpnt = Microsoft PowerPoint (If Installed)
winword = Microsoft Word (If Installed)
frontpg = Microsoft FrontPage (If Installed)
notepad = Notepad
wordpad = WordPad
calc = Calculator
msmsgs = Windows Messenger
mspaint = Microsoft Paint
wmplayer = Windows Media Player
rstrui = System Restore
netscp6 = Netscape 6.x
netscp = Netscape 7.x
netscape = Netscape 4.x
waol = America Online
control = Opens the Control Panel
control printers = Opens the Printers Dialog
cmd = Command Prompt
iexplore + "web address" = Internet Explorer
compmgmt.msc = Computer Management
dhcpmgmt.msc = DHCP Management
dnsmgmt.msc = DNS Management
services.msc = Services
eventvwr = Event Viewer
dsa.msc = Active Directory Users and Computers
dssite.msc = Active Directory Sites and Services
Windows key + E = Explorer
ALT + Tab = Switch between windows
ALT, Space, X = Maximize window
CTRL + Shift + Esc = Task Manager
Windows key + Break = System properties
Windows key + F = Search
Windows key + D = Hide/Display all windows
CTRL + C = copy
CTRL + X = cut
CTRL + V = paste
Also don't forget about the "Right-click" key next to the right Windows key on your keyboard. Using the arrows and that key can get just about anything done once you've opened up any program.
-------------------------
Keyboard Shortcuts:
-------------------------
[Alt] and [Esc] Switch between running applications
[Alt] and letter Select menu item by underlined letter
[Ctrl] and [Esc] Open Program Menu
[Ctrl] and [F4] Close active document or group windows (does not work with some applications)
[Alt] and [F4] Quit active application or close current window
[Alt] and [-] Open Control menu for active document
Ctrl] Lft., Rt. arrow Move cursor forward or back one word
Ctrl] Up, Down arrow Move cursor forward or back one paragraph
[F1] Open Help for active application
Windows+M Minimize all open windows
Shift+Windows+M Undo minimize all open windows
Windows+F1 Open Windows Help
Windows+Tab Cycle through the Taskbar buttons
Windows+Break Open the System Properties dialog box
---------------------------
Acessability shortcuts:
---------------------------
Right SHIFT for eight seconds........ Switch FilterKeys on and off.
Left ALT +left SHIFT +PRINT SCREEN....... Switch High Contrast on and off.
Left ALT +left SHIFT +NUM LOCK....... Switch MouseKeys on and off.
SHIFT....... five times Switch StickyKeys on and off.
NUM LOCK...... for five seconds Switch ToggleKeys on and off.
-----------------------
explorer shortcuts:
-----------------------
END....... Display the bottom of the active window.
HOME....... Display the top of the active window.
NUM LOCK+ASTERISK....... on numeric keypad (*) Display all subfolders under the selected folder.
NUM LOCK+PLUS SIGN....... on numeric keypad (+) Display the contents of the selected folder.
NUM LOCK+MINUS SIGN....... on numeric keypad (-) Collapse the selected folder.
LEFT ARROW...... Collapse current selection if it's expanded, or select parent folder.
RIGHT ARROW....... Display current selection if it's collapsed, or select first subfolder.
BACKSPACE[<-]...........To page up and traverse through different directory.
---------------------
internet browser:
---------------------
type in your address "google", then press [Right CTRL] and [Enter]
add www. and .com to word and go to it
---------------------
For Windows XP:
---------------------
Copy. CTRL+C
Cut. CTRL+X
Paste. CTRL+V
Undo. CTRL+Z
Delete. DELETE
Delete selected item permanently without placing the item in the Recycle Bin. SHIFT+DELETE
Copy selected item. CTRL while dragging an item
Create shortcut to selected item. CTRL+SHIFT while dragging an item
Rename selected item. F2
Move the insertion point to the beginning of the next word. CTRL+RIGHT ARROW
Move the insertion point to the beginning of the previous word. CTRL+LEFT ARROW
Move the insertion point to the beginning of the next paragraph. CTRL+DOWN ARROW
Move the insertion point to the beginning of the previous paragraph. CTRL+UP ARROW
Highlight a block of text. CTRL+SHIFT with any of the arrow keys
Select more than one item in a window or on the desktop, or select text within a document. SHIFT with any of the arrow keys
Select all. CTRL+A
Search for a file or folder. F3
View properties for the selected item. ALT+ENTER
Close the active item, or quit the active program. ALT+F4
Opens the shortcut menu for the active window. ALT+SPACEBAR
Close the active document in programs that allow you to have multiple documents open simultaneously. CTRL+F4
Switch between open items. ALT+TAB
Cycle through items in the order they were opened. ALT+ESC
Cycle through screen elements in a window or on the desktop. F6
Display the Address bar list in My Computer or Windows Explorer. F4
Display the shortcut menu for the selected item. SHIFT+F10
Display the System menu for the active window. ALT+SPACEBAR
Display the Start menu. CTRL+ESC
Display the corresponding menu. ALT+Underlined letter in a menu name
Carry out the corresponding command. Underlined letter in a command name on an open menu
Activate the menu bar in the active program. F10
Open the next menu to the right, or open a submenu. RIGHT ARROW
Open the next menu to the left, or close a submenu. LEFT ARROW
Refresh the active window. F5
View the folder one level up in My Computer or Windows Explorer. BACKSPACE
Cancel the current task. ESC
SHIFT when you insert a CD into the CD-ROM drive Prevent the CD from automatically playing.
-------------------------------------------------------
Use these keyboard shortcuts for dialog boxes:
-------------------------------------------------------
To Press
Move forward through tabs. CTRL+TAB
Move backward through tabs. CTRL+SHIFT+TAB
Move forward through options. TAB
Move backward through options. SHIFT+TAB
Carry out the corresponding command or select the corresponding option. ALT+Underlined letter
Carry out the command for the active option or button. ENTER
Select or clear the check box if the active option is a check box. SPACEBAR
Select a button if the active option is a group of option buttons. Arrow keys
Display Help. F1
Display the items in the active list. F4
Open a folder one level up if a folder is selected in the Save As or Open dialog box. BACKSPACE
If you have a Microsoft Natural Keyboard, or any other compatible keyboard that includes the Windows logo key and the Application key , you can use these keyboard shortcuts:
Display or hide the Start menu. WIN Key
Display the System Properties dialog box. WIN Key+BREAK
Show the desktop. WIN Key+D
Minimize all windows. WIN Key+M
Restores minimized windows. WIN Key+Shift+M
Open My Computer. WIN Key+E
Search for a file or folder. WIN Key+F
Search for computers. CTRL+WIN Key+F
Display Windows Help. WIN Key+F1
Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain. WIN Key+ L
Open the Run dialog box. WIN Key+R
Open Utility Manager. WIN Key+U
----------------------------------------
Accessibility keyboard shortcuts:
----------------------------------------
Switch FilterKeys on and off. Right SHIFT for eight seconds
Switch High Contrast on and off. Left ALT+left SHIFT+PRINT SCREEN
Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK
Switch StickyKeys on and off. SHIFT five times
Switch ToggleKeys on and off. NUM LOCK for five seconds
Open Utility Manager. WIN Key+U
-------------------------------------------------------
Shortcuts you can use with Windows Explorer:
-------------------------------------------------------
Display the bottom of the active window. END
Display the top of the active window. HOME
Display all subfolders under the selected folder. NUM LOCK+ASTERISK on numeric keypad (*)
Display the contents of the selected folder. NUM LOCK+PLUS SIGN on numeric keypad (+)
Collapse the selected folder. NUM LOCK+MINUS SIGN on numeric keypad (-)
Collapse current selection if it's expanded, or select parent folder. LEFT ARROW
Display current selection if it's collapsed, or select first subfolder. RIGHT ARROW
----------------------------------------
Shortcut Keys for Character Map:
----------------------------------------
After you double-click a character on the grid of characters, you can move through the grid by using the keyboard shortcuts:
RIGHT ARROW (Move to the right or to the beginning of the next line)
LEFT ARROW (Move to the left or to the end of the previous line)
UP ARROW (Move up one row)
DOWN ARROW (Move down one row)
PAGE UP (Move up one screen at a time)
PAGE DOWN (Move down one screen at a time)
HOME (Move to the beginning of the line)
END (Move to the end of the line)
CTRL+HOME (Move to the first character)
CTRL+END (Move to the last character)
SPACEBAR (Switch between Enlarged and Normal mode when a character is selected)
WISE WORDS:A lie never lives to be old.
How To Set Up Proxies In Your Browser
===================================
How to set up proxies in your browser, (!!!!be anonymous and make the passes last longer...!!!!!!
===================================
In Internet Explorer
===================================
Click "Tools", then "Internet Options", the in the "connections" Tab, click the "LAN Setup" Button in the bottom. There is a "Proxy Servers", tick the "Use a proxy....." and then enter the proxy in the bigger textbox and the port (the part that comes after the ":") in the smaller textbox. Hit okay, and then go to
CODE
www.whatismyip.com
to see if the proxy is now your IP.
===================================
In OPERA
===================================
Click "Files", then "Preferences", then "Network", then click the button "Proxy Servers", tick "HTTP", fill in with the proxy:port, click okay and that's it! Don't forget to check with
CODE
www.whatismyip.com
===================================
In Firefox
===================================
Tools -> Options
Then click the General Icon
Then the "Connection Settings..." button
Then click the "manually configure proxies" radio button, and enter the proxy address and port in the HTTP Proxy area.
Don't forget to check with
CODE
www.whatismyip.com
CODE
www.proxy4free.com
www.safeproxy.org
www.megaproxy.com
www.guardster.com
www.silenter.com
www.anonymizer.com
Happy Anonymous surfing!
To be clear: if I give you 255.255.255.255:8080, that means 255.255.255.255 is the proxy and 8080 is the port
To Optain Fresh and new proxies,u can alvays check Google...
Friday, August 10, 2007
Change Default Location of i386 Folder
1. Insert your windows xp cd
2. Click on, “Perform Additional Tasks”
3. Now click on, “Browse this CD”
4. Look for the I386 folder, right-click on the folder and copy.
5. Go into, “My Computer”
6. Right click on you C: drive and paste.
How can I change the default location of the i386 folder?
After installing Windows 2000 or XP, if you ever need to add a component to it (like DHCP etc.) it always asks you for the CD, even if you copy the i386 files to your local drive. Can I fix this?
Yes you sure can.
1. Open the registry editor and go to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup
2. Highlight the Setup folder.
3. On the right pane, locate the SourcePath.
4. Double-click the SourcePath and replace the drive letter in the box to C:\ (if you copied the files to your C:\ drive). Make sure it's C:\ and not C:\i386.
5. Close the registry editor.
6. If the system ever needs files from the i386 folder, it will automatically look in the C:\i386 folder.
You can also do the trick with Windows 2000 and XP Professional client computers that were installed from a shared folder on your network, but do not copy the i386 folder to the local drive of each computer. Instead, copy the i386 folder to a share located on a network server. Edit the registry for the Windows 2000 or XP Pro machines and make it point to the UNC path of the network server.
Also, if you installed from a RIS server, keep the RIS server running. Your system is smart enough to grab the files from the RIS server when it needs extra files.
This tip works for service packs too. You'll notice at the registry string from step #1 that it says service packsourcepath. Extract the SP from the command prompt to a folder on your hard drive using the w2ksp# -x switch, make the path in the registry where you put the files, and you won't have to go fishing for service pack disks again.
Well folks, from now on you should never be asked for that cd again…
*BTW, after all my writing, I found a program that takes the place of having to modify the registry manually. It’s called BanishCD from AnalogX. Here’s what they have to say:
One of the best ways to make Windows more convenient is to copy the CAB files from the CD onto your harddrive, so whenever you install any new hardware, you don't need to put the CD in your system. Unfortunately, Windows still ASKS for the CD, and you need to point it to where you copied the CAB files to, until now...
AnalogX BanishCD is a small utility that allows you to change the path that Windows will look for the CAB files. Normally, the only way this could be done would be to modify the registry manually, which is a very tricky process, and if you make a mistake it can be hard to repair. With BanishCD, you can quickly browse through your system and select the path; and just in case you make a mistake it will store the original path!
Download BanishCD from here:
CODE
hxxp://www.analogx.com/contents/download/system/banishcd.htm
Restore JPG,JPEG,JPE Default File Associations
This reg file will restore the default file associations.
1. Copy the following (everything in the box) into notepdad.
QUOTE
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\.jpe]
"PerceivedType"="image"
@="jpegfile"
"Content Type"="image/jpeg"
[HKEY_CLASSES_ROOT\.jpe\OpenWithProgids]
"jpegfile"=hex(0):
[HKEY_CLASSES_ROOT\.jpe\PersistentHandler]
@="{098f2470-bae0-11cd-b579-08002b30bfeb}"
[HKEY_CLASSES_ROOT\.jpeg]
"PerceivedType"="image"
@="jpegfile"
"Content Type"="image/jpeg"
[HKEY_CLASSES_ROOT\.jpeg\jpegfile]
[HKEY_CLASSES_ROOT\.jpeg\jpegfile\ShellNew]
[HKEY_CLASSES_ROOT\.jpeg\OpenWithProgids]
"jpegfile"=hex(0):
[HKEY_CLASSES_ROOT\.jpeg\PersistentHandler]
@="{098f2470-bae0-11cd-b579-08002b30bfeb}"
[HKEY_CLASSES_ROOT\.jpg]
"PerceivedType"="image"
@="jpegfile"
"Content Type"="image/jpeg"
[HKEY_CLASSES_ROOT\.jpg\jpegfile]
[HKEY_CLASSES_ROOT\.jpg\jpegfile\ShellNew]
[HKEY_CLASSES_ROOT\.jpg\OpenWithProgids]
"jpegfile"=hex(0):
2. Save the file as assoc_fix.reg
3. Double click the file to import into your registry.
NOTE: If your anti-virus software warns you of a "malicious" script, this is normal if you have "Script Safe" or similar technology enabled.
Free Access To Websites Without Registering
-http://bugmenot.com/
and type the URL of the website you want to log into.
Examples:
-http://www.nytimes.com/, -http://www.winnetmag.com/
etcetera.
Another (and better) way is changing the user agent of your browser to:
Googlebot/2.1+
-http://www.googlebot.com/bot.html
This is very easy in Mozilla's Firefox. Download and install the User Agent Switcher from
-http://www.chrispederick.com/work/firefox/useragentswitcher/
and add the Googlebot user agent.
Have fun, Guys!!!
[Now this kicks ass, was just browsing entire forum without even needing to login to view restricted areas, and it works on other sites .]
10 Fast and Free Security Enhancements
1. Check Windows Update and Office Update regularly. (_http://office.microsoft.com/productupdates); have your Office CD ready. Windows Me, 2000, and XP users can configure automatic updates. Click on the Automatic Updates tab in the System control panel and choose the appropriate options.
2. Install a personal firewall.
Both SyGate and ZoneAlarm offer free versions.
3. Install a free spyware blocker.
SpyBot Search & Destroy. SpyBot is also paranoid and ruthless in hunting out tracking cookies.
4. Block pop-up spam messages in Windows NT, 2000, or XP by disabling the Windows Messenger service (this is unrelated to the instant messaging program). Open Control Panel | Administrative Tools | Services and you'll see Messenger. Right-click and go to Properties. Set Start-up Type to Disabled and press the Stop button. Bye-bye, spam pop-ups! Any good firewall will also stop them.
5. Use strong passwords and change them periodically. Passwords should have at least seven characters; use letters and numbers and have at least one symbol. A decent example would be g9izKro@l. This will make it much harder for anyone to gain access to your accounts.
6. If you're using Outlook or Outlook Express, use the current version or one with the Outlook Security Update installed. The update and current versions patch numerous vulnerabilities.
7. Buy antivirus software and keep it up to date. If you're not willing to pay, try Grisoft AVG Free Edition. And doublecheck your AV with the free, online-only scanners available at _www.pandasoftware.com/activescan and _http://housecall.trendmicro.com.
8. If you have a wireless network, turn on the security features: Use MAC filtering, turn off SSID broadcast, and even use WEP with the biggest key you can get. For more, check out our wireless section or see the expanded coverage in Your Unwired World in our next issue.
9. Join a respectable e-mail security list, such as the one found at our own Security Supersite at _http://security.ziffdavis.com, so that you learn about emerging threats quickly and can take proper precautions.
10. Be skeptical of things on the Internet. Don't assume that e-mail "From:" a particular person is actually from that person until you have further reason to believe it's that person. Don't assume that an attachment is what it says it is. Don't give out your password to anyone, even if that person claims to be from "support."
Search Google For RAPIDSHARE Links
Paste this into the google search window (not the adress bar):
site:rapidshare.de -filetype:zip OR rar daterange:2453402-2453412
* this searches the site rapidshare.de for any file that is rar or zip, and
has been indexed between 1-11 February.
dvd site:rapidshare.de -filetype:zip OR rar daterange:2453402-2453412
* this is the same search but it specifically searches for "dvd" with the same
search criteria, so any app posted with the word dvd in it will be found.
There are mainly three criteria to keep in mind when doing this search.
1. site: your site of choice to search
2. filetype: filetypes you wanna search,if you put a "OR" after the first
filetype you can add more.
3. daterange: (start date-enddate)
* this uses the "julian calendar", converter can be found here:
Code:
src="http://pagead2.googlesyndication.com/pagead/show_ads.js">
http://aa.usno.navy.mil/data/docs/JulianDate.html
Thursday, August 9, 2007
Safely Editing The Registry
Click on Start | Run and enter Regedit to launch the Registry editor. To back up an individual key you plan to edit, navigate to the key and right-click on it. Choose Export from the menu, and save the key to a REG file. Open the REG file in Notepad and insert a few comment lines that describe the source and purpose of the tweak. (To create a comment line, simply put a semicolon at the start of the line.)
Now go ahead and make all the changes to Registry keys and values specified by the tip you're applying. Any time you add a new key or value, make a note of it with another comment line in the REG file. When you're done, save the REG file and close Notepad.
If later you want to undo this Registry tweak, just double-click on the REG file and confirm that you want to add it to the Registry. This will restore any deleted keys or values and will restore the original data for any values whose data was changed. Note that this will not remove new keys or values that were added; that's why you need to make comments about such changes.
Right-click on the REG file and choose Edit, which will open it in Notepad. Check for comments about keys or values that were added, and if you find any, use Regedit to delete them. You can delete the REG file itself once you've completed this process
How to Bypass Web Filters
Lets pretend for a moment that the Internet is made up of 26 websites, A-Z. The web filter blocks your browser from accessing sites X-Z, but not sites A-W. Simply make the browser think you’re going to A-
W. There are a variety of ways to do this:
Proxy Servers:
This is a list of http proxies. These sites may not be up forever, so you may need to search for “free http proxy” or “public proxy servers” or other similar terms.
Proxy server lists:
• https://www.aliveproxy.com
• https://www.multiproxy.org
• https://www.publicproxyservers.com/index.html
• https://www.tehbox.com/proxy
• https://www.proxz.com
• https://www.proxy4free.com/index.html
• https://free-proxies.com
Now that you have a list of proxies, you would open IE (internet explorer) and click on Tools > Internet Options > Connections > LAN Settings > Advanced. Enter the address and port of one of the servers from the list in the proper area (http) and make sure the “use a proxy server for your LAN” option is selected. Remember to replace the proxy and port at your terminal to the original when you're done.
*Note: Some proxies listed may not work, and this method may decrease your surfing speed. By trying various entries, you’ll find one that works, or works faster.
The infamous translation trick:
Go to a web page translation site and use their services to “translate a page to English” thus accessing the blocked page through their trusted site.
You’ll notice that several translation sites are blocked, but by using less popular ones, this method can still be effective. Here is a list of some translation services. Again, these sites may not be up forever, so you may need to search for them.
• https://babelfish.altavista.com
• https://world.altavista.com
• https://translation.langenberg.com
• https://freetranslation.com/web.thm
Url Scripting:
Url scripting is the easiest method. It works on a select few web filters and is based on the same principal as the translation trick. By typing and address like “www.yahoo.com@www.restricted_site.com the filter will not go into effect as it recognizes the trusted site (in this case yahoo.com)
Other tricks:
Simply open the command prompt and type:
Ping restricted.com [restricted.com means obviously the site your being restricted.]
At this point you can take down the IP address (ex. 216.109.124.73) and enter it into the browser. If access to the command prompt is also restricted, see “How to bypass restrictions to get to the command prompt.” If this article has been taken from information leak, then know that it involves anything from opening the browser, selecting view > source, then saving it as X.bat and opening it to opening a folder or browser and typing in the location of cmd.exe depending on the OS. I will not go into further, as this a completely different topic.
Use http://restrictedsite.com as referring to it as a secured site may confuse the filter.
Note: These are ancient methods that many new filters defend against, but still may be applicable in your situation. If not, a little history never hurt anyone.
Web based Proxies:
Another one of the easier, yet effective methods include web based proxies. These are simple in the fact that you just enter the restricted address and surf! Some of these have some restrictions, like daily usage limits, etc but you can also use another proxy (perhaps one that sucks, like a text only) to bypass their restrictions as well. Here is a list of some:
• https://proxify.com
• https://www.anonymizer.com/index.cgi
• https://www.guardster.com/
• https://anonymouse.ws/anonwww.html
• https://www.the-cloak.com/login.html
• https://www.megaproxy.com/freesurf
• https://www.anonymizer.ru
• https://nadaily.com/cgi-bin/nph-proxyb.cgi
• https://www.userbeam.de/cgi-bin/nph-userbeam.cgi
• https://www.free2.surffreedom.com/nph-free.cgi
Proxy Programs:
There are many proxy programs that allow you to surf anonymously that are more or less based on the same topics we’ve covered here. I’ve added them just to cover the topic thoroughly:
• https://www.hotscripts.com/Detailed/28480.html
• https://www.inetprivacy.com/a4proxy.......a4proxy/anonymous-grc.htm
• https://www.orangatango.co........rangatango.com/home/index.ie.html
• https://www.steganos.com
• https://www.anonymization.net
Making your own CGI proxy server:
Making your own proxy server may come in handy, but I personally find that simply uploading a txt file/w a list of proxies to a free host makes for a much easier and headache free solution. If you don’t know PERL, there is code out there to help you set it up. Check out these sites for more info:
• https://httpbridge.sourceforge.net]hxxp://httpbridge.sourceforge.net
• https://www.jmarshall.com/tools/cgiproxy]hxxp://www.jmarshall.com/tools/cgiproxy
•https://www.manageability.org/bl.....org/blog/stuff/op...en-in-java/view
Admin Access:
When all else fails, you can simply take over the PC and alter or delete the damn filter. This method varies according to the OS (operating system) you are dealing with. Please see “Hacking Windows NT” for more information. If this tutorial has been taken from information leak, then I will go as far as to say it involves booting the PC in another OS, copying the SAM file and cracking it using a program like saminside or LC5 rather than start a whole new topic within one.
How To Restrict Login Hours Allowed
Below are some examples:
1 - net user Joanna /time:M-F,08:00-17:00
2 - net user Ninja /time:M-F,8am-5pm
3 - net user Echelon /time:M,4am-5pm;T,1pm-3pm;W-F,8:00-17:00
4 - net user Shine /time:all (this one means this user can always log on)
Note:You can only restrict when a user can log on to the system. On a stand alone computer, there is no way to force a user to log off when their hours expire, without a third party script or software.
Wednesday, August 8, 2007
Set Google as your Default Search in IE
CODE:
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main]
"Search Page"="http://www.google.com"
"Search Bar"="http://www.google.com/ie"
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\SearchURL]
""="http://www.google.com/keyword/%s"
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Search]
"SearchAssistant"="http://www.google.com/ie"
1. Save the file as Google.reg
2. Double click to import to your registry.
NOTE: If your anti-virus software warns you of a "malicious" script, this is normal if you have "Script Safe" or similar technology enabled.
WISE WORDS: The best throw with the dice is to throw them away.
Keep Your Computer Clean Always
All of you must have to agree with me on something and that is Computing can only be fun when you when your computer runs smooth and faster. Right? So try to keep it clean on both hardware & software level. Only a clean computer runs faster and lasts longer. Its important to take care about this major investment of yours. There are few things you can do which are very easy but extremely effective to keep your computer in health. After all as long as it would last, its only going to serve you.
Here is some tips to keep the hardware runs smoothly...
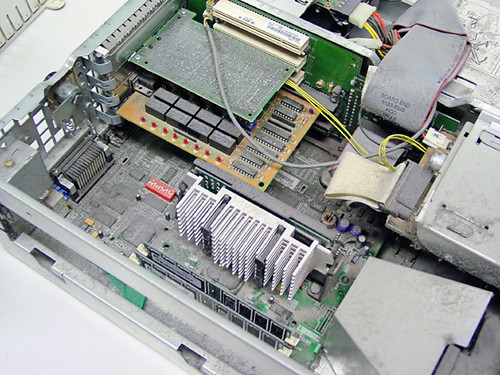
1. Clean out the dust particles. Dust is the silent PC killer. Every once and a while you should open it up and clean it out. Some experts suggests using vacuum cleaner for this purpose but i don’t like to think otherwise. Because some dust cleaners are so powerful in sucking air that might harmful. You can of always use dust remover.
2.Keep your PC cool place. You should always make sure that you keep your computer in a well ventilated area. By doing this you help keep the PC cool and, therefore, will prolong the life of your buddy’s hardware.
3.Develop a habit of purchasing quality hardware.Try to get good quality parts when you buy new components for your PC. If you get components always prefer buying from esteemed manufacturers you can be sure that you will get good technical support and the parts will be well made and not cause problems with other existing hardware.
4.Make sure various power supply is uniform. Take note that each plug is plugged into surge protected outlet strips which are plugged into a UPS (Uninterrupted Power Supply).
5.All items should be properly installed in your computer. When you replace any hardware with a new one, you must install the proper drivers for the new component.
6. Special care should be taken while cleaning the monitor screen. Turn off the monitor before you try any attempt to clean it. Use a soft, clean cloth something like t-shirt and spray a little window cleaner on the cloth. Do not spray cleaner on the monitor or laptop screens. Apply the little wet cloth across the display area first, then the frame and outer casing. This will surly improve the visibility of the images. Of course
use a quality cleaner for this purpose.
7. Consider replacing old UPS, power cables and other important electrical components that may be worn. If you had several outages while using your UPS, you may consider replacing it. If the equipment is at least three years old, then at least inspect it. Some items last longer, but like an old car, you should watch them.
Now time for some software operations to maintain the operating system of your PC...
1. Run the defragmenter utility at least once every month or two. In Windows XP, this can be done by going to your Start menu -> Programs -> Accessories -> System Tools -> Disk Defragmenter. The defragmenter will help ensure that your files are located at the right place on the hard drive and should boost the overall speed of your computer.
2. Run a disk scan to check for hard drive issues. Open My computer -> Right click on the drive [c:.d:,e:..] -> Properties -> tools -> Check Now. This option will check that specific drive for errors and fix it.
3. Empty your recycle bin once in a month.
4. Delete your Internet files.
5. Clear your browsing history.
6. Delete your cookies.
7. Clean up old & temporary files. When you install/uninstall software frequently it can leave many unwanted files in temporary and system folders. In Windows XP, you should run the Disk Cleanup utility once and a while to clean things up. This utility can be found by clicking the Start menu -> All Programs -> Accessories -> System Tools -> Disk Cleanup.
8. Should full system scan can for viruses once in a fortnight. Viruses can cause your computer to be slow or not work at all. You should always have a good virus scanner installed and keep it up to date. Some well known virus scanners are Norton, McAfee and AVG.
9. Scan for other malware. Other malware can include spyware, adware, key loggers, and Trojan horses. These pieces of software can get installed without your knowledge when you install another program or visit a website. They can cause your PC to slow down considerably. Spybot Search & Destroy and Adware are two well known malware scanners.
That’s all for now. Later someday we will dive into extensive details of PC maintenance & troubleshooting. We will see that not tough you thought before.
Blank Scrap
To write a blank scrap ... just do this...
Invisible Scraps
Hey!.....It is very easy to send invisile scraps now!
Just follow the steps as follows!
1)Got to someone's scrap book!
2)Write there [ i ] without spaces!
3)Click On SUBMIT!
WOW!
You have just sent an invisible scrap!!!!!
WISE WORDS: The clothes makes the man
Hello Friends
I have created this blog to share my knowledge about some of the lesser known areas or sometimes referred as 'Mystic Lands' of computer operations.If you are a newbie in computers & looking for someone who can help you to become an advance computer user, then you came to the right place. Congratulations!!!!
Oh, so you think, you are not a 'newbie'? Well, that's great!!!!!! But still you have to agree with me that your knowledge is not absolute too. So you can find lots of information, which i think, you would like to term as 'tricky 'n useful' and help you to hone your computer skills farther.
I am going to post new articles almost on a daily basis. So keep visiting and maybe you will find something that you thought never can be done in your windows box.
No Text Icons
Right click the icon and select "Rename"
Now hold the "Alt" key and type "255" and hit Enter
Or you can do it by holding "Alt" key and type "0160" and hit Enter
NOTE : It may only work with the keypad numbers and not the number keys on top of the keyboard.
Install Xp From Dos
it yet try these:
Install Windows XP from the hard drive with Windows 98 already installed:
Boot Windows 98
Insert the XP CD into your CD reader
Explore Windows XP through My Computer
Copy i386 folder to C:\
Go into C:\i386 folder and double click on winnt32.exe to launch the setup from the hard drive
Install Windows XP from DOS (ie. no OS on a new hard drive):
Boot with a Windows 98 Start Up disk
Insert the Windows 98 CD into the CD reader
Run smartdrv.exe from the Win98 directory on the windows 98 CD (file caching)
Type cd.. to back up to the root directory
Insert Windows XP CD into the CD reader
Copy the i386 folder to C:\
Go into C:\i386 folder on C: and type winnt.exe to launch the setup from the hard drive.
How to modify any exe files
1) Don't try to modify a prog by editing his source in a dissasembler.Why?
Cause that's for programmers and assembly experts only.
try to view it in hex you'll only get tons of crap you don't understand.
First off, you need Resource Hacker(last version). It's a resource editor-
very easy to use, You can download it at h**p://www.users.on.net/johnson/resourcehacker/
2) Unzip the archive, and run ResHacker.exe. You can check out the help file too
3) You will see that the interface is simple and clean. Go to the menu FileOpen or press Ctrl+O to open a file. Browse your way to the file you would like to edit. You can edit *.exe, *.dll, *.ocx, *.scr and *.cpl files, but this tutorial is to teach you how to edit *.exe files, so open one.
4) In the left side of the screen a list of sections will appear.
The most common sections are
-String table;
-RCData;
-Dialog;
-Cursor group;
-Bitmap;
-WAV.
*Icon: You can wiew and change the icon(s) of the program by double-clicking the icon section,chossing the icon, right-clicking on it an pressing "replace resource". After that you can choose the icon you want to replace the original with.
*String table: a bunch of crap, useful sometimes, basic programming knowladge needed.
*RCData: Here the real hacking begins. Modify window titles, buttons, text, and lots more!
*Dialog:Here you can modify the messages or dialogs that appear in a program. Don't forget to press "Compile" when you're done!
*Cursor group: Change the mouse cursors used in the program just like you would change the icon.
*Bitmap: View or change images in the programs easy!
*WAV:Change the sounds in the prog. with your own.
5) In the RCData,Dialog,Menu and String table sections you can do a lot of changes. You can modify or translate the text change links, change buttons, etc.
TIP: To change a window title, search for something like: CAPTION "edit this".
TIP: After all operations press the "Compile Script" button, and when you're done editing save, your work @ FileSave(Save as).
TIP: When you save a file,the original file will be backed up by default and renamed to Name_original and the saved file will have the normal name of the changed prog.
TIP: Sometimes you may get a message like: "This program has a non-standard resource layout... it has probably been compressed with an .EXE compressor." That means that Resource Hacker can't modify it because of it's structure.